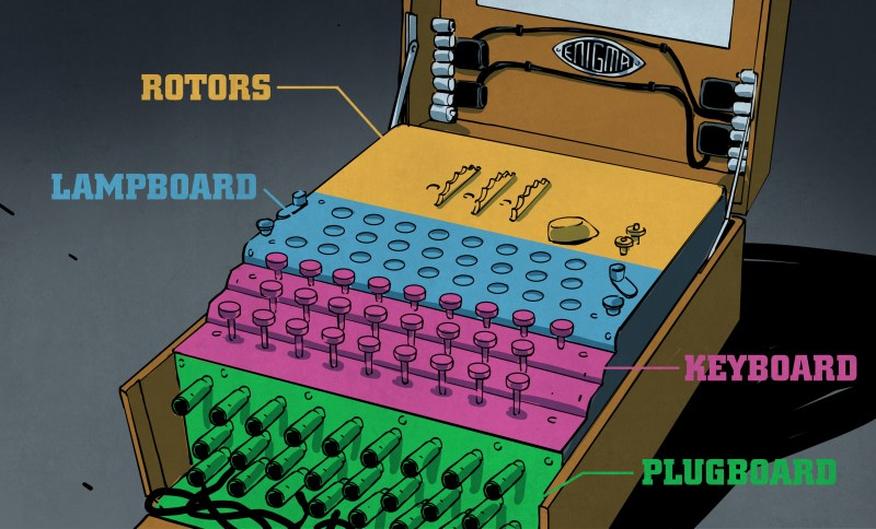
The real Enigma machine encrypted messages using a complex electromechanical system. When an operator pressed a key on its keyboard, an electrical circuit completed through several rotating rotors. Each rotor substituted one letter for another and moved after each key press, changing the substitution pattern continuously. This mechanism ensured the same letter would be encoded differently each time it appeared in a message, making interception and decryption without proper settings extremely challenging.

An Enigma machine featured three or sometimes four rotors, each embedded with intricate wiring that scrambled input signals. Pressing a key sent electricity through the rotors, which transformed the signal to illuminate a lamp indicating the encrypted letter. After each key press, at least one rotor rotated, altering the wiring paths for the next letter. This dynamic stepping created a vast number of possible cipher combinations.
- Each rotor had 26 electrical contacts connected internally in a unique wiring pattern.
- Rotors rotated in intricate sequences similar to an odometer, dramatically increasing cipher complexity.
- A plugboard at the machine’s front allowed swapping pairs of letters to add another encryption layer.
For communication, both sender and receiver had to synchronize their machines with identical settings. These settings included the order of the rotors, the initial position of each rotor, plugboard connections, and occasionally ring settings on the rotors themselves.
Enigma operators received daily or monthly codebooks listing these settings. For example, a codebook might instruct using rotors II, IV, and I with starting positions 06, 17, and 26. These settings were essential; without them, decryption was nearly impossible.
Different German military branches (Army, Air Force, Navy) used distinct networks with unique Enigma configurations. For example, the Navy had separate procedures and even introduced a four-rotor Enigma for U-boat communications, making their ciphers more complex than the standard three-rotor versions used by other branches.

Security hinged on strict secrecy about these settings. Physical possession of an Enigma machine was worthless without the specific daily or monthly key settings. Settings were closely guarded; operators used codebooks under tight controls and were instructed to destroy them at risk of capture. Naval settings were sometimes printed in water-soluble ink for quick disposal.
Breaking Enigma required more than mechanical possession—it demanded insight into the machine’s configuration. Thus, the Allies valued pinches—captured codebooks or key materials immensely. These materials were obtained during raids, submarine captures, or opportunistic missions. Examples include the capture of settings from the patrol boat Krebs and the submarine U-110, which provided vital cryptographic intelligence.

These pinches enabled cryptanalysts at Bletchley Park to understand German procedures and weaken Enigma’s security. They combined this information with weaknesses in German operating habits to reconstruct key settings when direct captures were unavailable.
| Aspect | Details |
|---|---|
| Machine Components | Three or four rotors, plugboard, keyboard, lamps |
| Encryption Process | Signal passes through rotors and plugboard to scramble letters |
| Rotor Movement | Rotors step after each keystroke, changing the substitution pattern |
| Settings | Rotor order, initial positions, plugboard wiring, ring settings |
| Security | Codebooks, strict secrecy, destruction if compromise risk |
| Variants | Navy used different procedures; four-rotor Enigma for U-boats |
Despite these layers of protection, Enigma was vulnerable due to procedural flaws and the repeated use of predictable key settings. Bletchley Park analysts exploited these weaknesses alongside captured materials to read a significant amount of through traffic. Their work shortened the war by providing critical intelligence on enemy operations.

The introduction of the four-rotor Navy Enigma posed fresh challenges, requiring new techniques and additional pinches to break its codes. This ongoing arms race between Enigma operators and Allied codebreakers demonstrated the complexity and importance of secure communication during wartime.
- Encryption involved electrical substitution through rotating rotors and a plugboard.
- Both ends needed identical machine settings to encode and decode messages.
- Strict secrecy of settings was critical for maintaining Enigma’s security.
- Captured codebooks and materials were invaluable for breaking codes.
- Different military branches had unique Enigma configurations and procedures.
- Bletchley Park combined cryptographic intelligence and analytical skill to succeed.
In the Imitation Game Movie, How Did the Real Enigma Machine Work?

In short: The Enigma machine was an electromechanical puzzle box turning messages into seemingly random letters through spinning rotors, but its real power was in the shared secret settings; without those, even the cleverest codebreakers were at a loss. Let’s unravel how this fascinating device operated, beyond the Hollywood glamor.
The Imination Game movie showcases Alan Turing’s heroic work deciphering Enigma-encrypted messages during World War II. But real life is more complex and, frankly, much more interesting. The Enigma wasn’t just Turing’s solo project; it was a massive team effort at Bletchley Park, building on Polish intelligence achievements before the war.

How the Enigma Machine Actually Works: The Basics
Imagine a typewriter connected to a series of rotating discs called rotors. When a single key presses, an electrical current zigzags through this labyrinth, lighting up one letter on a lamps panel. But here’s the kicker: each key press turns at least one rotor, scrambling the wiring routes for next time. So if you press ‘A’ twice, the light might first show ‘G’ then ‘Z’.
This rotor mechanism was Enigma’s secret sauce—a clever way to keep messages changing continuously. Most machines used three rotors; some went a step further with a fourth. But don’t get lost in the gears—this oversimplifies a bit. Different branches of the military had slightly different Enigmas. For the full tech deep dive, plenty of dedicated sites break down wiring patterns and signal paths.
The All-Important Settings
Here’s a twist that might surprise you. The Enigma machine itself was no good unless both sender and receiver set their machines identically.
That meant using the exact rotors in the exact order (like rotors II, IV, and I), each turned to precise starting positions (say 06, 17, and 26). These configurations weren’t chosen on a whim; they were carefully issued in secret codebooks, often changing monthly.
Think of these settings as the key to the cipher lock. Without these, the machine was mere hardware. The military’s “password” was this detailed procedure, not a simple word.
Keeping Settings Secure Was a Matter of Life and Death
Counterintuitively, many fictional tales emphasize stealing the physical Enigma machine itself. In reality, spies needed those key sheets more desperately than the gadget. If you had the settings of a particular day or unit, you could read their messages.
Operators knew this well. If capture was a threat, they burned their instruction sheets or, at sea, discarded ink that dissolved in water. Strict “need to know” rules kept these settings closely guarded to prevent leakage.
Captured Materials Were the Holy Grail
Bletchley Park’s codebreakers weren’t just guessing; they struck gold with “pinches”—captured cryptographic materials from German vessels or raids. For example, capturing settings from the submarine U-110 was like finding a secret map through a maze.
Every piece of information—whether entire codebooks or fragmentary procedures—helped the team build decoding strategies that went beyond brute force. These wins were rare and precious, like solving a puzzle with half the pieces missing.
Why It Wasn’t Just Alan Turing
Though The Imitation Game paints a bold picture, cracking Enigma was a collective mission. Polish cryptologists had already made vital breakthroughs before the war. Bletchley Park was a hive of brilliant minds—mathematicians, linguists, and technicians collaborating tirelessly.
Moreover, the Germans kept upping their game—introducing a four-rotor Enigma for the Navy’s U-boats, which scrambled codes more fiercely. The relentless back-and-forth was less like a sprint and more like an intellectual war of attrition.
What Can We Learn from the Real Enigma?
The Enigma machine’s story offers lessons well beyond WWII espionage. It highlights the importance of procedural security alongside technology. Even the most sophisticated device fails without secure operational discipline—think of it as your password’s secret sauce.
It also demonstrates how collaboration and incremental progress can overcome seemingly invincible problems. The polish groundwork, Bletchley’s collective intellect, and sometimes plain luck capturing materials remind us that breakthrough is rarely a solo act.
Ever wonder if, today, this kind of code-breaking challenges still exist? Absolutely. Encryption remains at the frontline of cybersecurity battles worldwide. The Enigma’s legacy is alive in modern cryptography, reminding us that cracking codes is as much art as science.
In Summary
- The Enigma machine scrambled messages through rotors that shifted electrical signals with every key press.
- Successful encryption and decryption relied on both machines sharing perfectly matched settings—rotors, order, and start points.
- Settings were issued securely, tightly guarded, and disposed of carefully to avoid enemy capture.
- Captured codebooks fuelled Allied breakthroughs, but breaking Enigma was a complex, ongoing battle involving many hands, not just Turing’s genius.
Next time you watch The Imitation Game, remember it’s a thrilling glimpse into a giant human puzzle. The Enigma’s mechanics are deceptively simple, yet behind that simplicity lies a labyrinth of secrets, strategy, and collaboration that shaped history.



